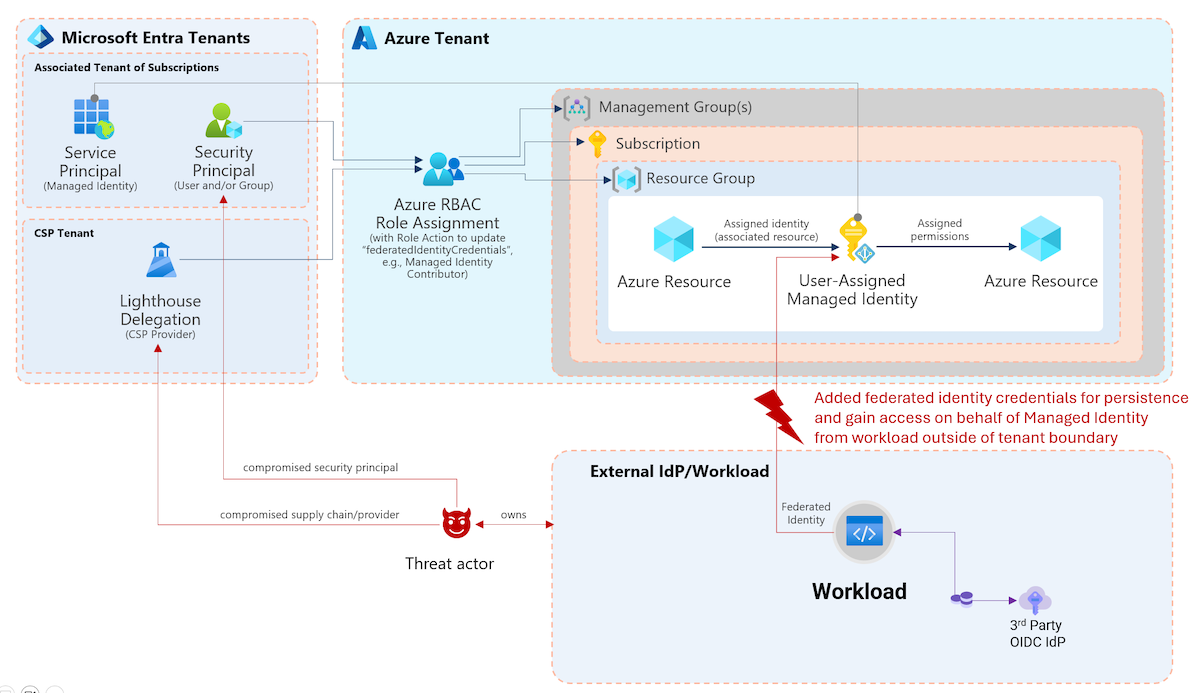
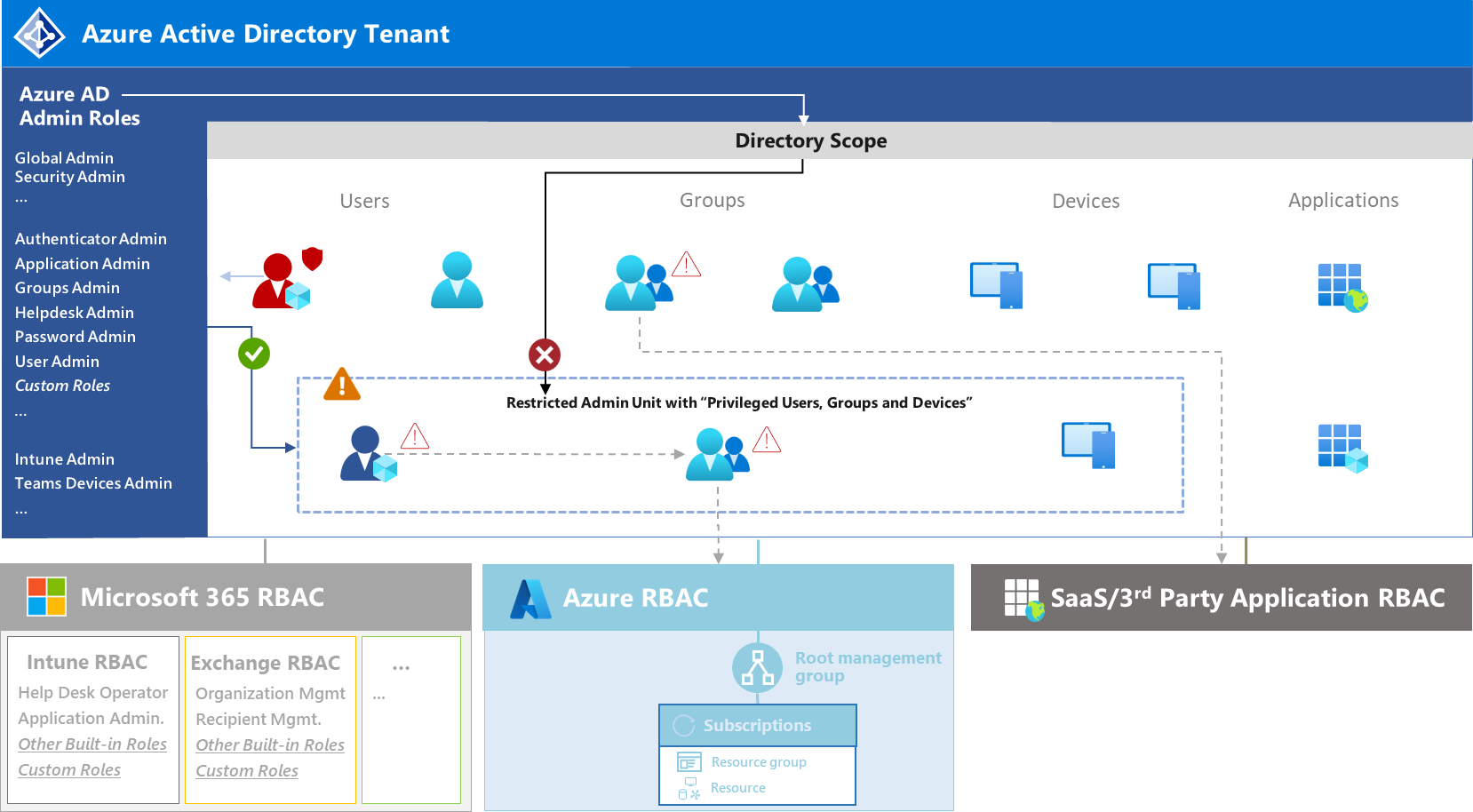
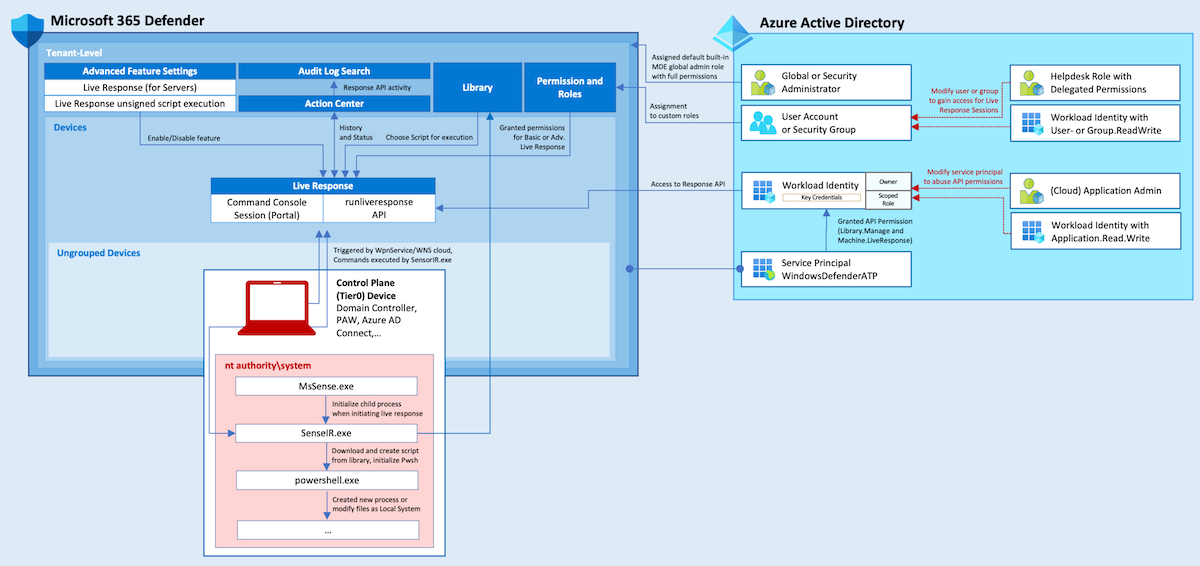
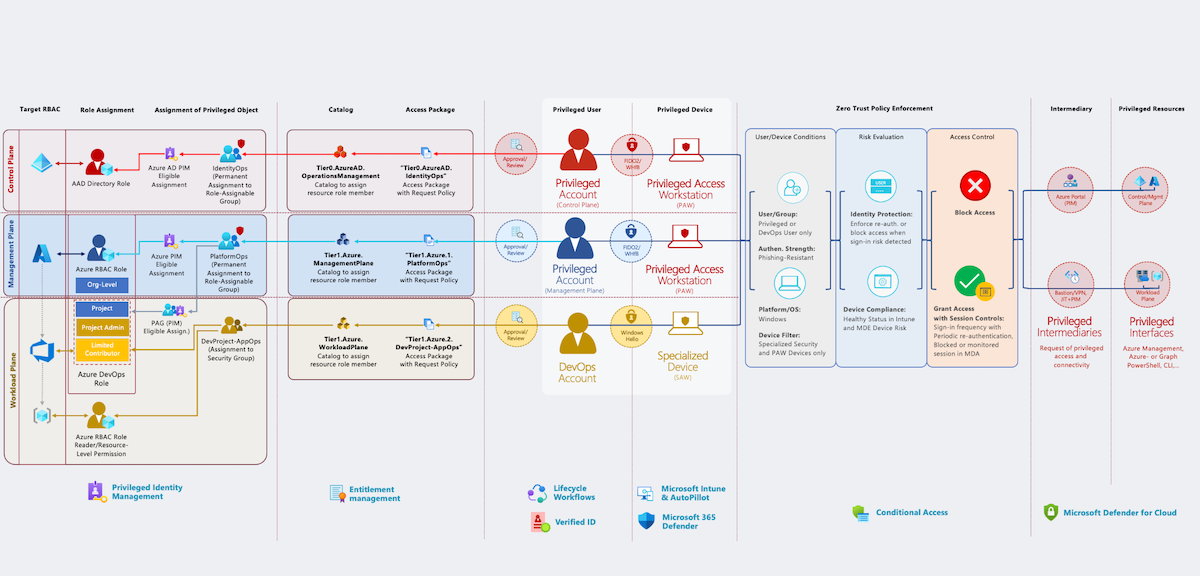
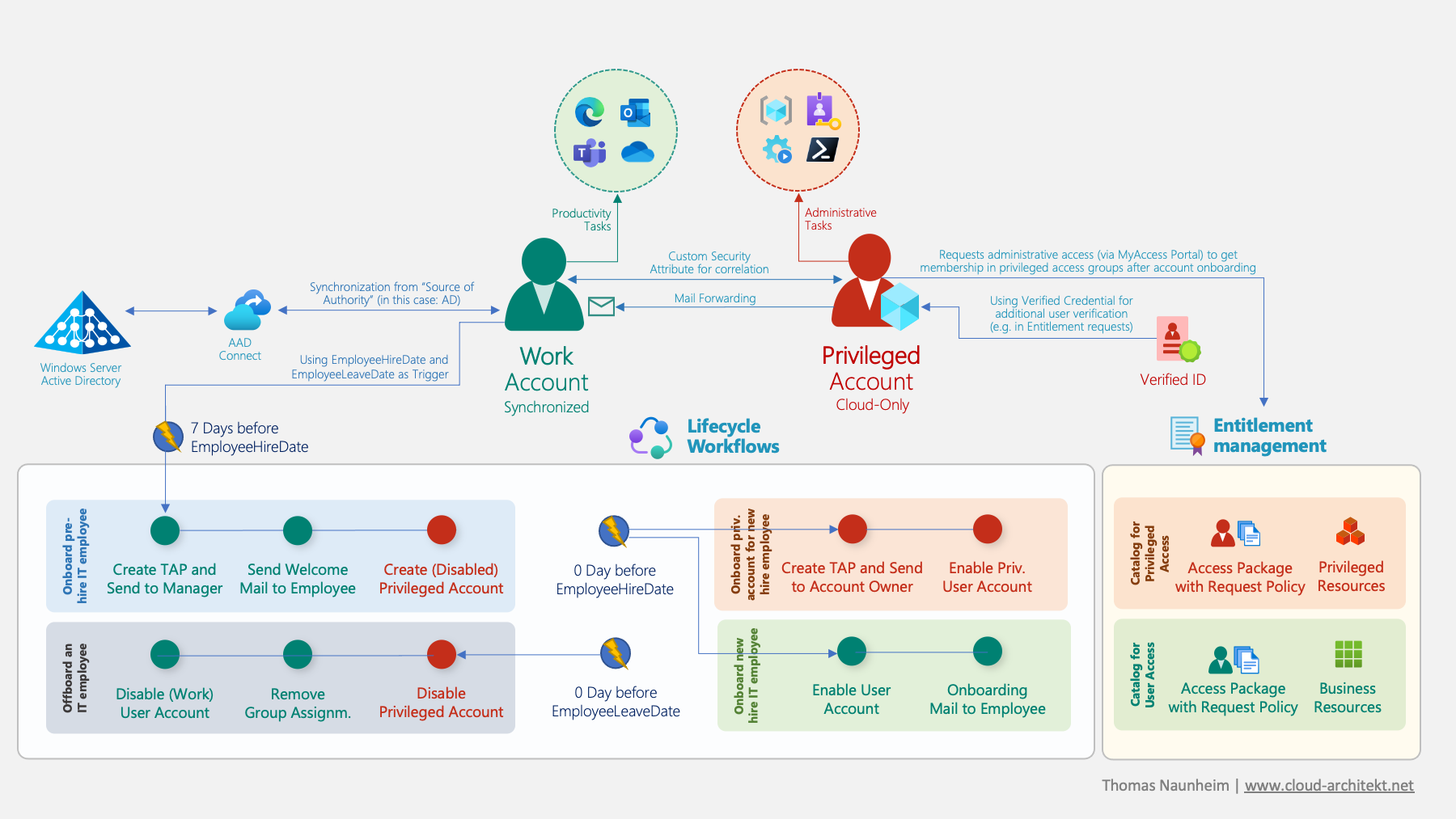
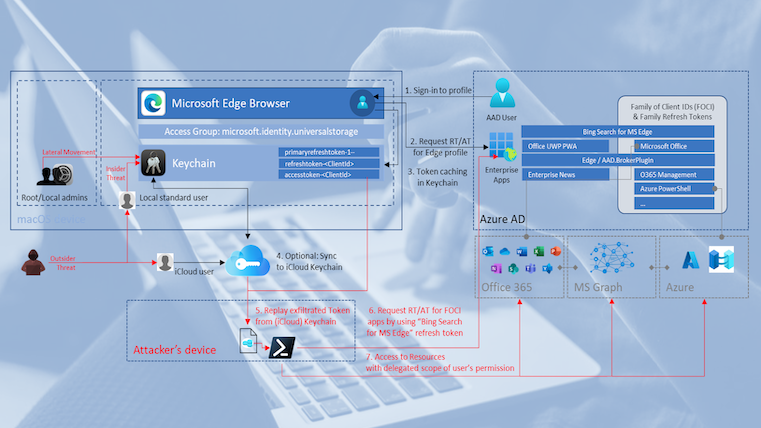
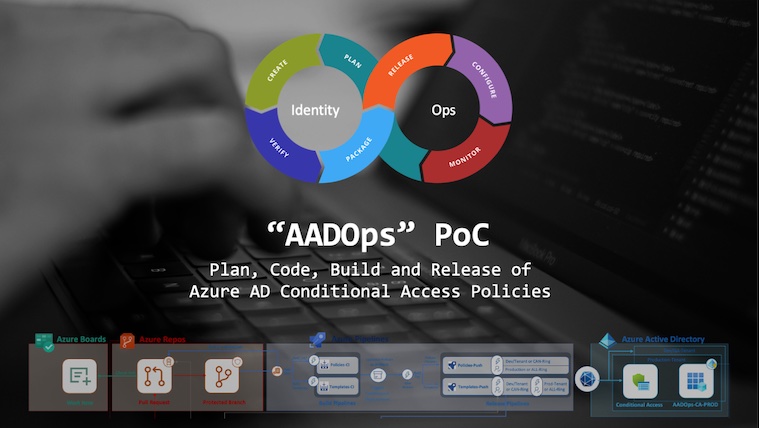
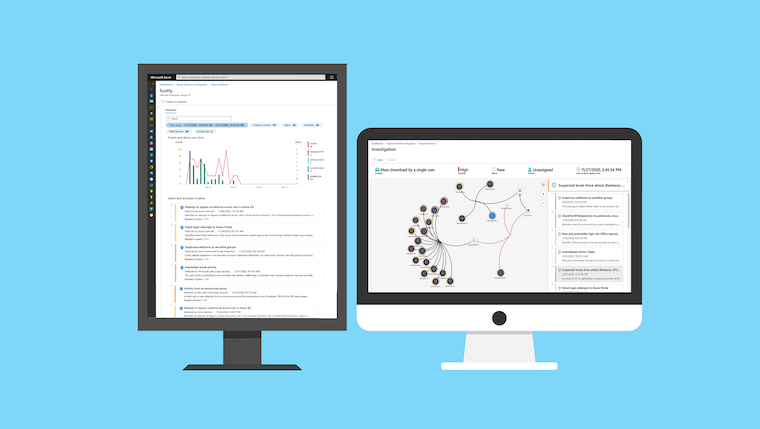
Analyzing Workload Identity Activity Through Token-Based Hunting
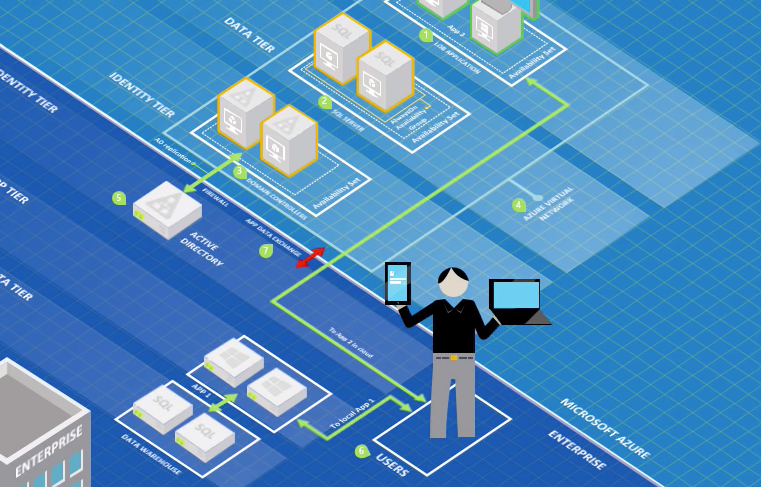
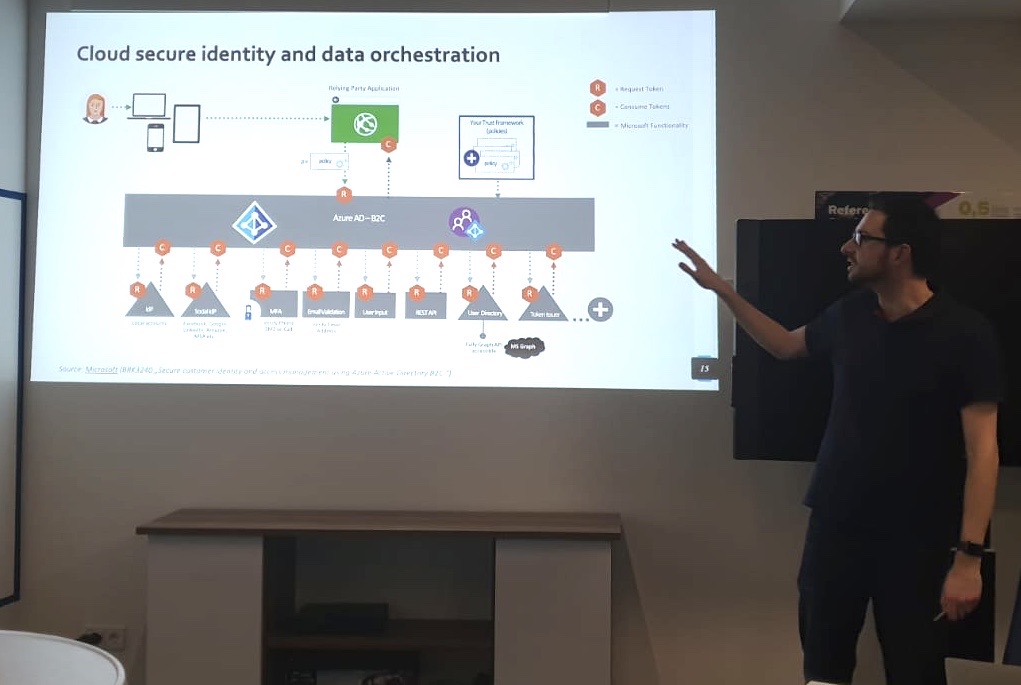
This post introduces the MicrosoftCloudWorkloadActivity KQL function and shows how to hunt token-based activity of workload identities across Microsoft cloud workloads. It covers key parameters, filtering strategies, and example queries for detecting unusual usage and anomalies, especia...