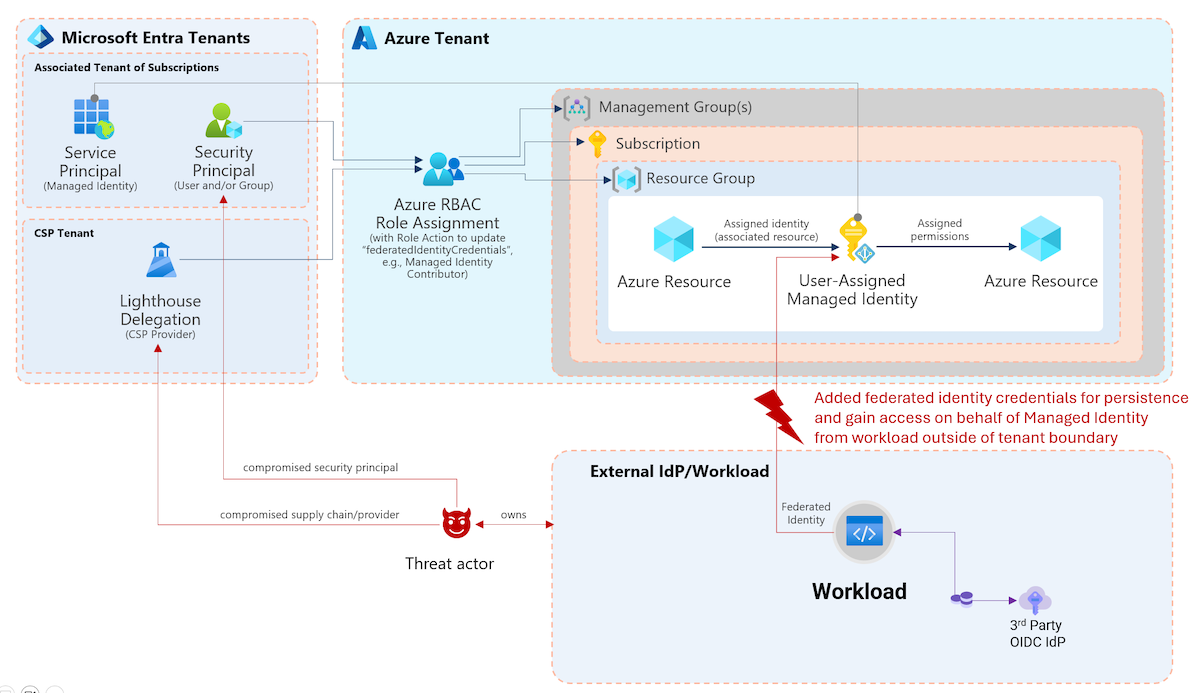
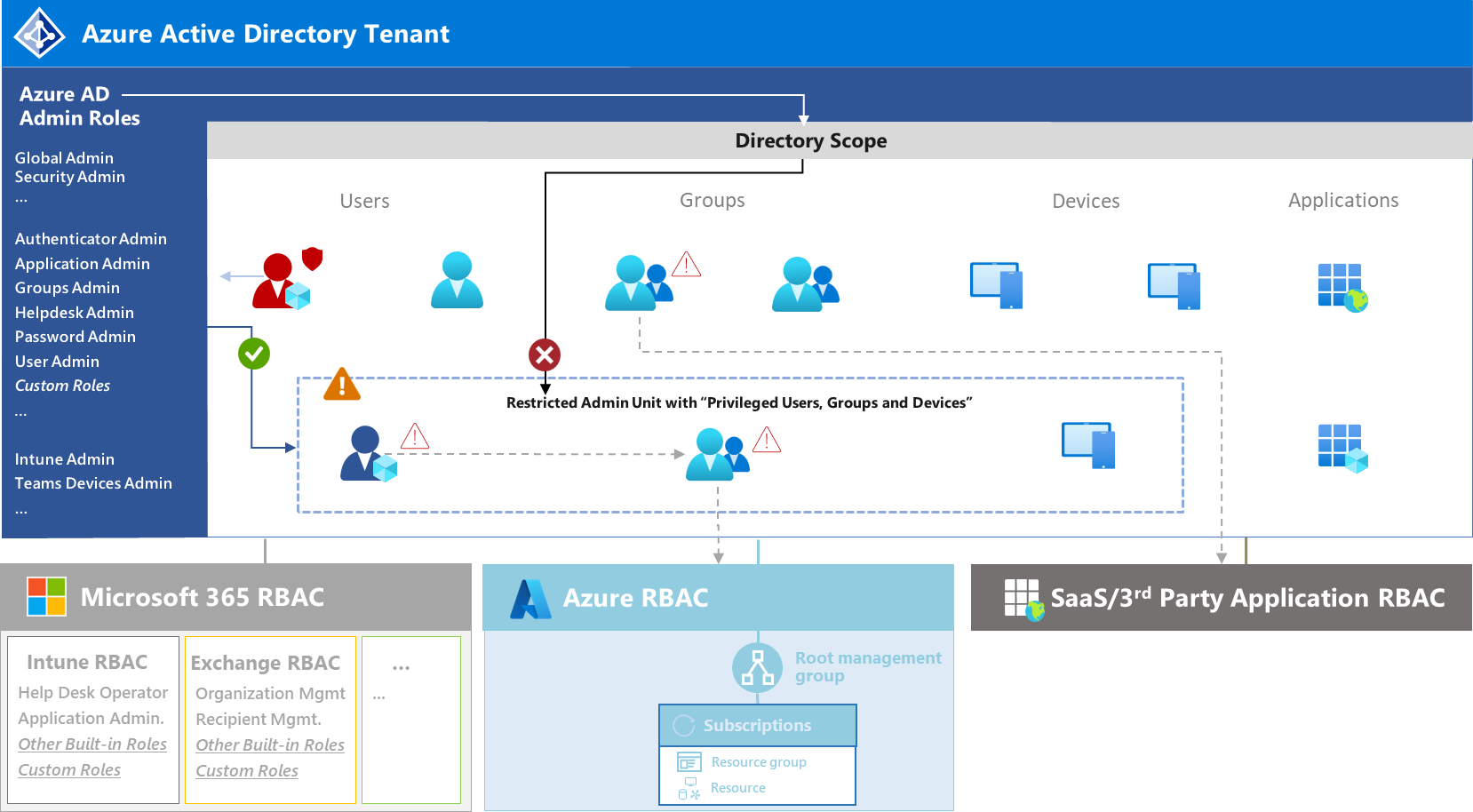
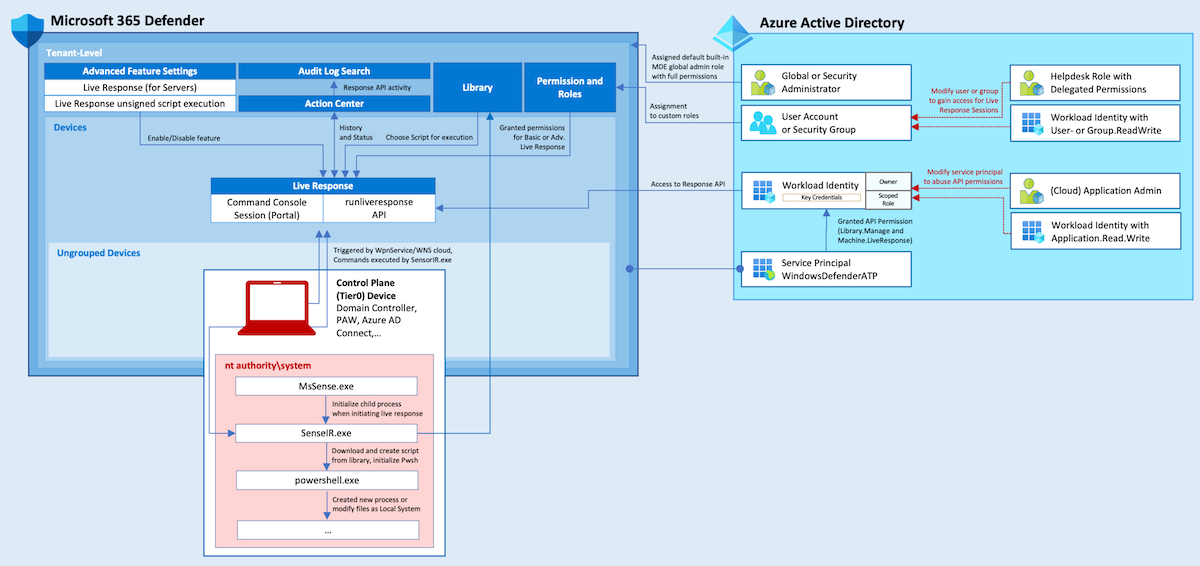
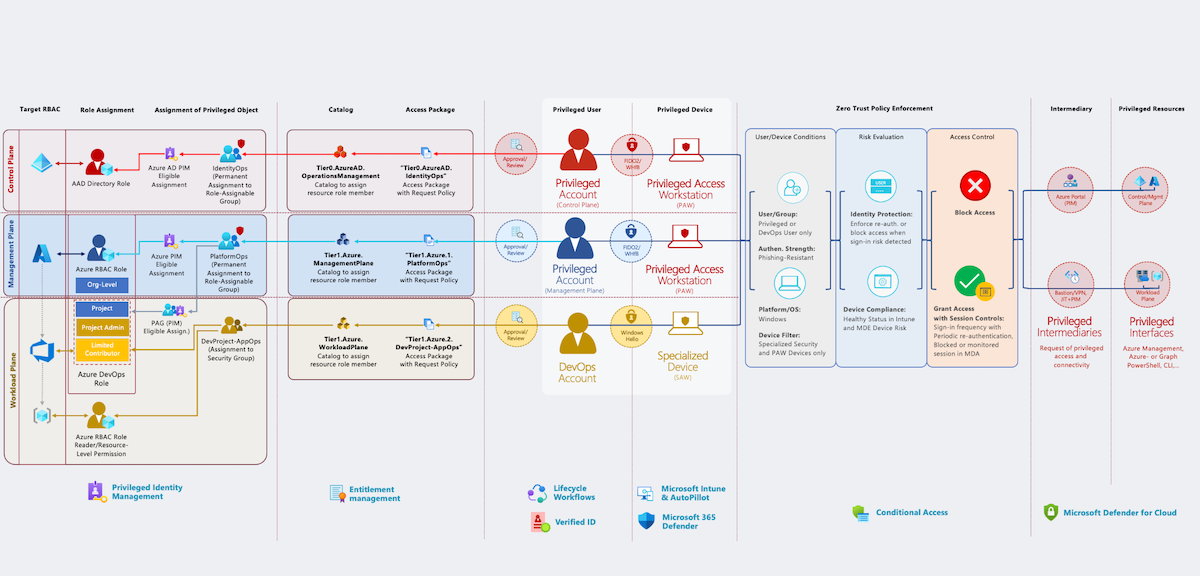
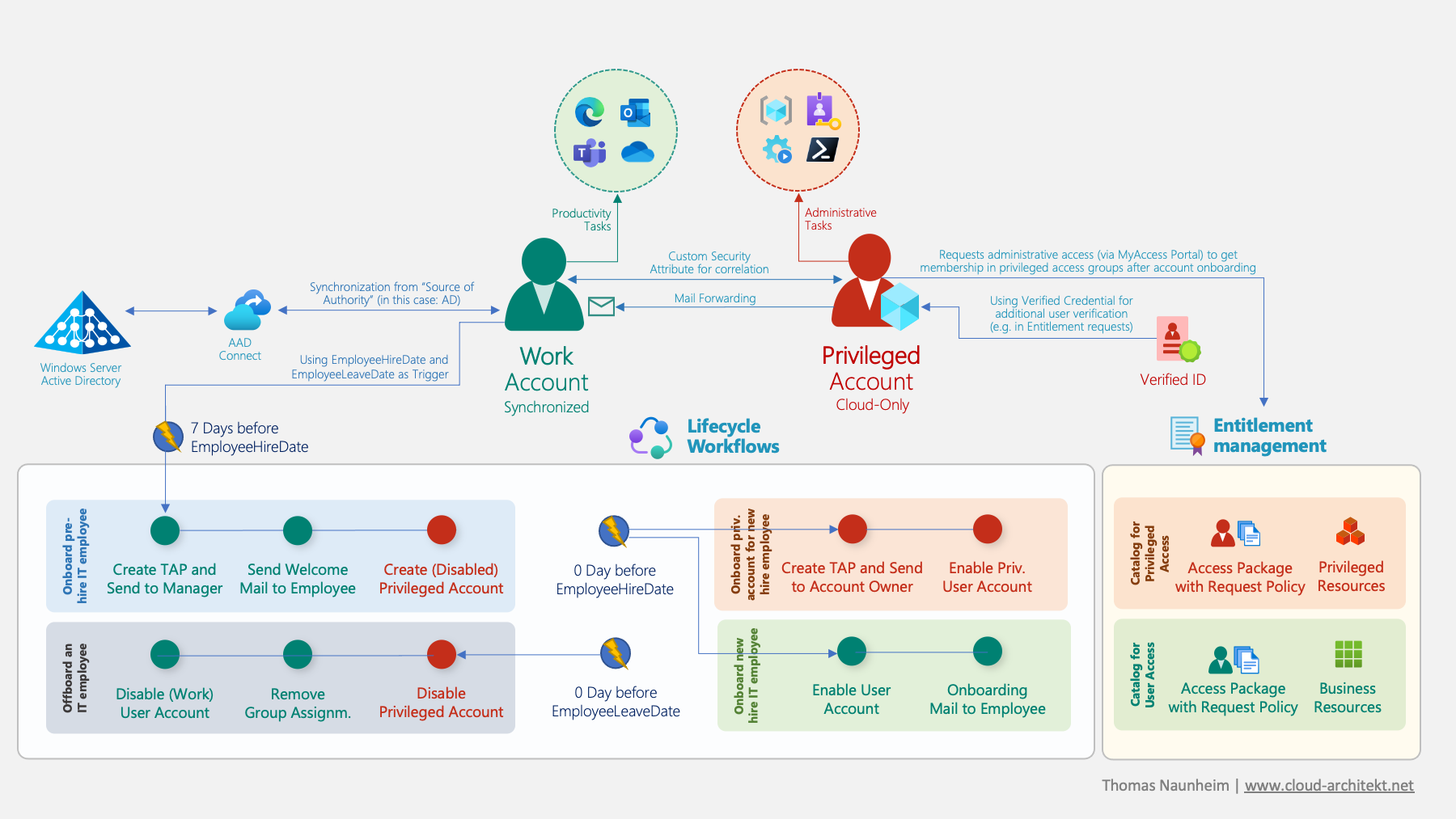
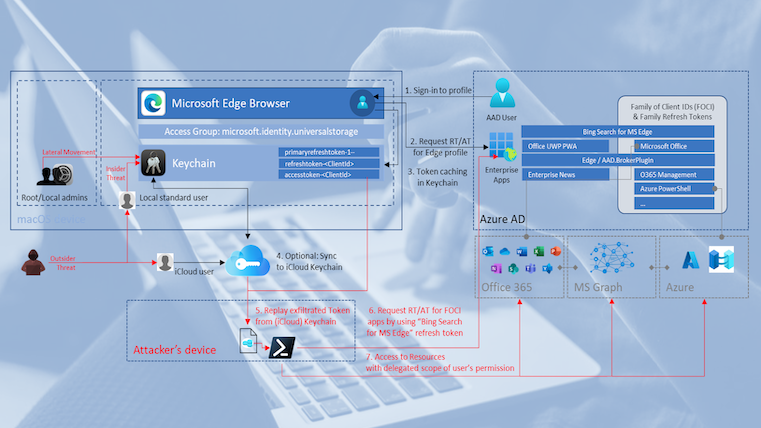
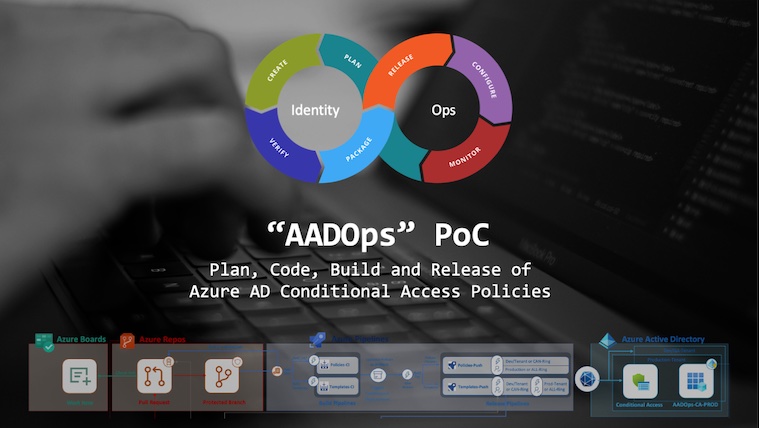
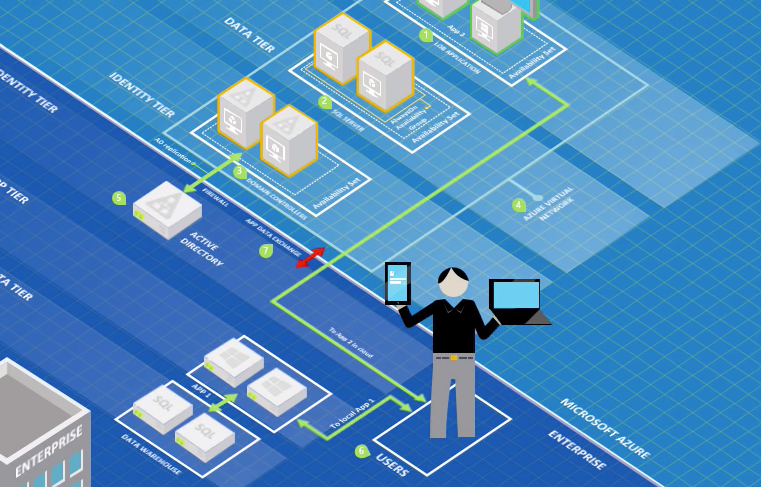
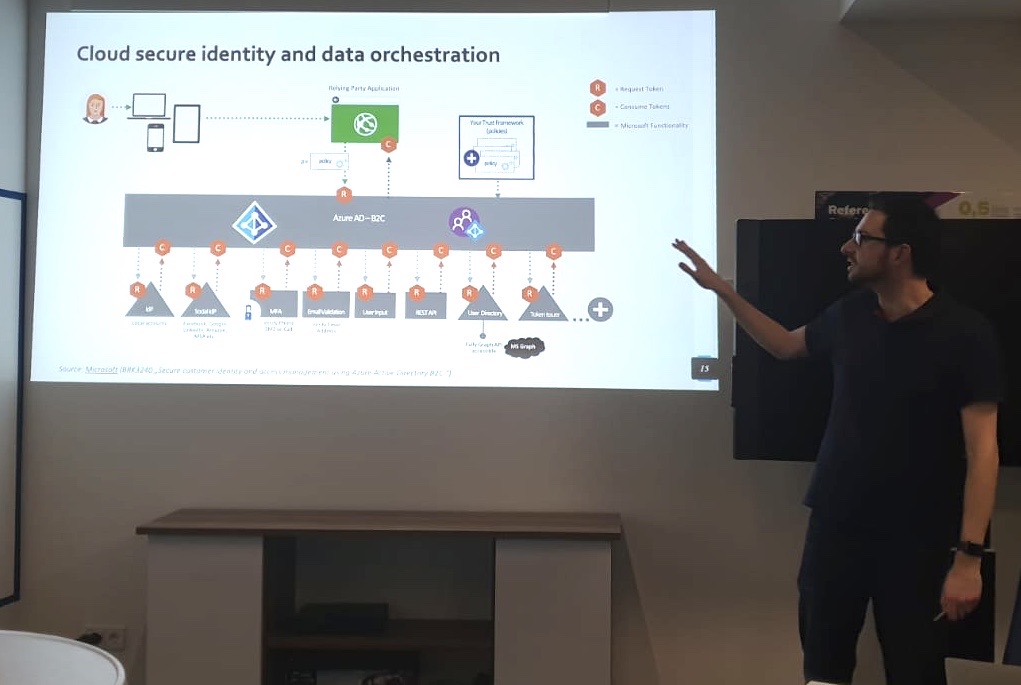
Identify and prevent abuse of Managed Identities with Federated Credentials from unauthorized entities
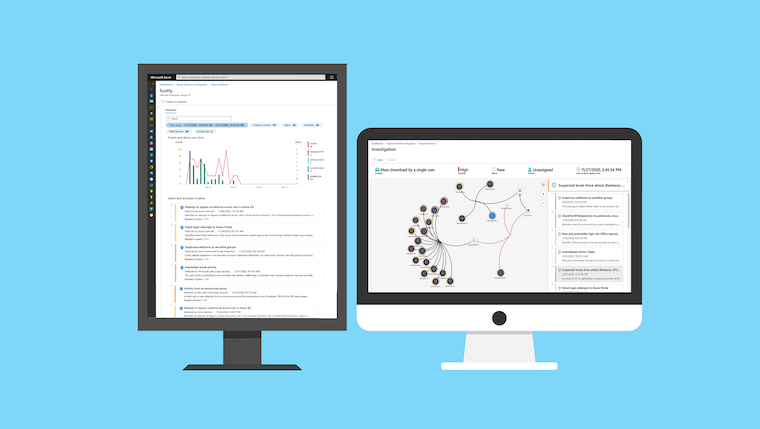
In this article, I would like to point out options to identify, monitor and avoid persistent access on Managed Identities privileges by adding federated credentials on User-Assigned Managed Identities (UAMI) from malicious or unauthorized entities. We will also have a quick look at atta...