Top articles:
Microsoft Entra ID Workload Identity blog post series
Do you like to learn more about Workload Identities? Check out my blog post series which covers management and security aspects of non-human identities…
Events and slides from my community talks
Overview about upcoming speaker engagements on meetups or conferences but also download links to my slides from past talks and list of sessions which I like to share with the community.
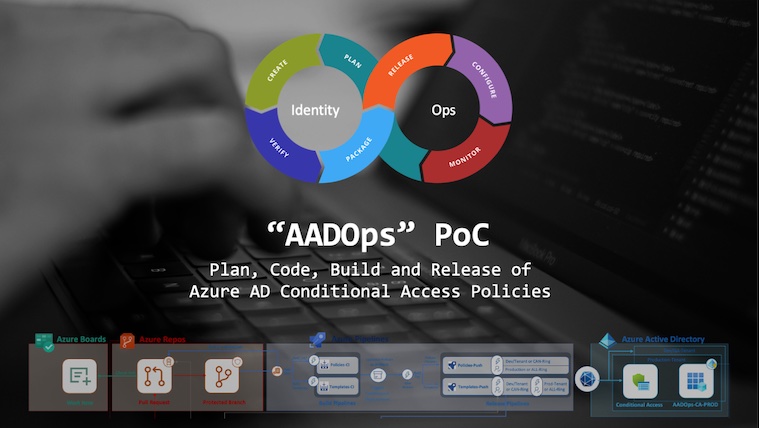
AADOps: Operationalization of Conditional Access
AADOps is a personal study and research project which sets out to demonstrate how “operationalization” of Azure AD in Azure DevOps could look like. Learn more about Conditional Access automated deployment.